September 2, 2020
Steering Clear of Scams
Contents
Volume 14, Issue 9
September 2020
Click here for a PDF version of this month's issue.
Steering Clear of Scams
Written by Deanna Pellegrino, Farm Credit East Information Security Specialist
The world of cyber security can be scary. With hacking, identity theft, fraud, phishing and other scams so prevalent, sometimes it can seem overwhelming. Although new threats are always on the rise, many scams can be avoided with a bit of knowledge and caution on your part.
Phishing
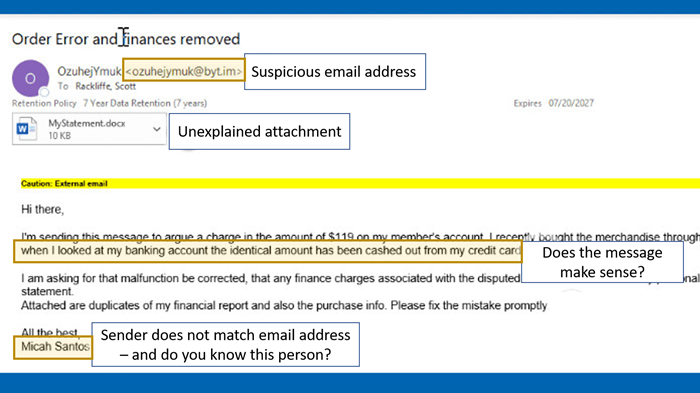
One common type of scam is called “phishing.” Phishing is an attempt by computer hackers to infiltrate your device or network via deceptive emails which often contain malicious links or software. Like actual fishing, these people often cast a broad net and then wait to see who “bites” or responds. Clicking on links or attachments in phishing emails could allow hackers access to your system or expose personal information. While all too common, and potentially dangerous, many phishing attempts are easy to spot if you know what to look for. Here are a few warning tips:
- Be wary of personal messages from people you don’t know, or business emails from companies you don’t do business with.
- Be aware that you can’t always trust the name the email appears to be from — email addresses can be “spoofed” — meaning a hacker sending the message pretends to be someone else, maybe someone you know. Hovering over the email is one way to identify the senders actual email address, but in any case, if an email looks like it’s from one of your contacts, but seems strange, double check to make sure it’s legitimate.
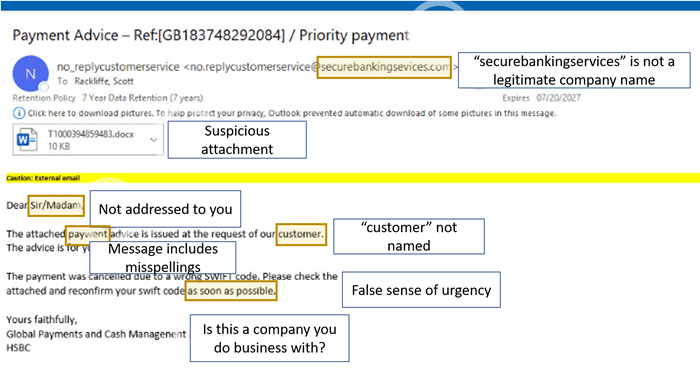
- Poor spelling and grammar are major red flags. Everyone makes the occasional mistake, but phishing emails are often riddled with misspellings and other basic errors.
- Note that links contained in emails may not always be what they seem. The text containing the link might say one thing, but actually take you somewhere else. Hovering over the link will often show the destination URL. If it doesn’t match what it is supposed to, don’t click on it.
- Remember the old adage, “If it seems too good to be true, it probably is.” It’s unlikely you’ve won a contest you don’t remember entering, received an inheritance from an unknown relative, or been granted a windfall from some mysterious government program. Free software can be risky as well. Some apps or programs offered for free on the internet are loaded with bugs and malware.
- Some scammers prey on people’s fears and may couple this with a claim of urgency to get you to act quickly without second-guessing your actions. A particularly insidious type of scam is an email suggesting that you have been hacked (or your computer is infected) and the sender wants you to do something (click a link, download something, make a call, send Bitcoin, gift cards or do something else) in order to remove a virus or prevent some kind of negative outcome. This is rarely the case. They are exploiting your fears to lure you into their trap.
- Another sneaky deception is an email telling you that your password or account has been compromised (or expired), and that you need to click on a link to verify it or change it. In reality, the link might take you to a fraudulent website where they collect your login credentials. These can be tricky, and hackers will often include official logos they have copied off the internet, or otherwise try to make the email appear genuine. Unless you are certain that the message is genuine, it’s a good practice to go to the business’s known website address and log in there, rather than using links.
Below are two examples of phishing attempts with labels on suspicious pieces of the email that can help you identify when you’re being phished.
Passwords
Using secure passwords is crucial in keeping data safe! Almost everything you do online requires a password, and it can be very confusing keeping track of them all. Here are a few tips to keep your passwords secure to ensure unauthorized parties cannot reach your sensitive information:
- For most people, some usernames and passwords are more critical to keep secure than others. For example, the password to log in to your favorite restaurant to order takeout online is less critical than the password for your investment accounts. For those critical accounts, here are a few best practices:
- Use unique passwords for each key account. That way, if your Netflix account is compromised, the hacker doesn’t have your bank account password as well.
- Consider using a secondary email for low-priority accounts, to keep your primary accounts more secure.
- Longer passwords are always better, as are those containing numbers or special characters. Try thinking of a sentence or phrase that is important to you and use those characters as your password. Example: You miss 100% of the shots you do not take translates to Ym100%otsydnt.
- If an account or password is compromised, change the log in credentials immediately and don’t use them again. One way to find out about at least some data breaches is Firefox Monitor (monitor.firefox.com). You can enter your email address and it will tell you if it finds it connected to any known data breaches.
Identity Theft
Be extremely careful with your Social Security number (SSN). There are certainly legitimate reasons why some businesses may need it, such as banks, government authorities and others. Typically applying for credit will require your SSN as well. However, be careful if entering it on a website. Be certain you are on a secure site (look for “https://” in the address, or a padlock icon, in some browsers). If a hacker gains access to your SSN, there is a lot they can do, including applying for credit or loans in your name, unemployment compensation, making bank transfers, stealing tax refunds, and more. Pay attention to your mail and your credit report. (You can get it free online at AnnualCreditReport.com, and yes, they will need your SSN to access it. You can get a free copy every 12 months from each of the three main credit bureaus. One trick is to request one of them every four months to space them out.)
Phone Scams
Finally, there are phone scams. Be aware that the IRS, Social Security Administration or other federal agencies do not initiate contact with taxpayers by phone (or social media) to request personal or financial information, nor will they call and threaten to arrest you or seize your bank accounts.
Just as with e-mail “from” addresses, caller’s phone numbers can be “spoofed” – and callers can pretend to be someone else. If a call from a company or government agency seems suspicious, hang up and call them back at a known number.
Stay vigilant!
Yes, it’s a scary world out there and there are plenty of people who would like to use your personal information for their gain. However, a dose of healthy skepticism will serve you better than paranoia. Most scams and identity theft attempts can be thwarted with a bit of caution.
For more information on how to avoid phishing and other scams, please access Farm Credit East’s Customer Assistance Program. This is a confidential, free resource available to all Farm Credit East customers that provides information related to personal finance, human resources, wellness, and many more topics, including how to protect yourself from cyber attacks and scams.
Editor: Chris Laughton
Contributors: Deanna Pellegrino, Tom Cosgrove and Chris Laughton
View previous editions of the KEP
Farm Credit East Disclaimer: The information provided in this communication/newsletter is not intended to be investment, tax, or legal advice and should not be relied upon by recipients for such purposes. Farm Credit East does not make any representation or warranty regarding the content, and disclaims any responsibility for the information, materials, third-party opinions, and data included in this report. In no event will Farm Credit East be liable for any decision made or actions taken by any person or persons relying on the information contained in this report.